AWS Secrets Manager is a service that makes it easier to rotate, manage, and retrieve database credentials. It is easy to configure Secrets Manager to rotate secrets automatically, which helps to meet the security needs. Secrets Manager offers built-in integrations for MySQL, PostgreSQL, and Amazon Aurora on Amazon RDS, and can rotate credentials for these databases. It is also possible to control access to secrets by using AWS Identity and Access Management (IAM) policies.
AWS Secrets Manager has many key features, mainly:
1. Rotate secrets safely: Secrets Manager helps in configuring secret rotation automatically without disrupting the applications. Secrets Manager offers built-in integrations for rotating credentials for Amazon RDS databases for MySQL, PostgreSQL, and Amazon Aurora. This rotation secret eliminates the need to manually update and redeploy secrets for applications. It also helps with custom rotation requirements by creating an AWS Lambda function to rotate other types of secrets.
Eg:- AWS Lambda function rotates OAuth tokens in mobile applications.
2. Monitor and audit easily: Secrets Manager integrates with AWS logging and monitoring services in order to meet the security and compliance requirements. There are two ways to do this.
a. AWS CloudTrail Logs: Helps to audit logs when Secrets Manager rotates a secret.
b. AWS CloudWatch Events: Helps in getting alerts when an administrator deletes a secret once event is configured.
Eg:- AWS CloudTrail Logs records all API calls for Secrets Manager as events like RotationStarted, RotationSucceeded, RotationFailed, etc.
Rotation: It is the process of periodically updating a secret to make it more difficult for an attacker to access the credentials. When Secrets Manager rotates a secret, it updates the credentials in both the secret and the database or service.
Steps to configure Secrets Manager.
Note: First launch an RDS Database before proceeding onto Secrets Manager configuration.
- To start with, open Secrets Manager from AWS Console and select Store a new Secret.
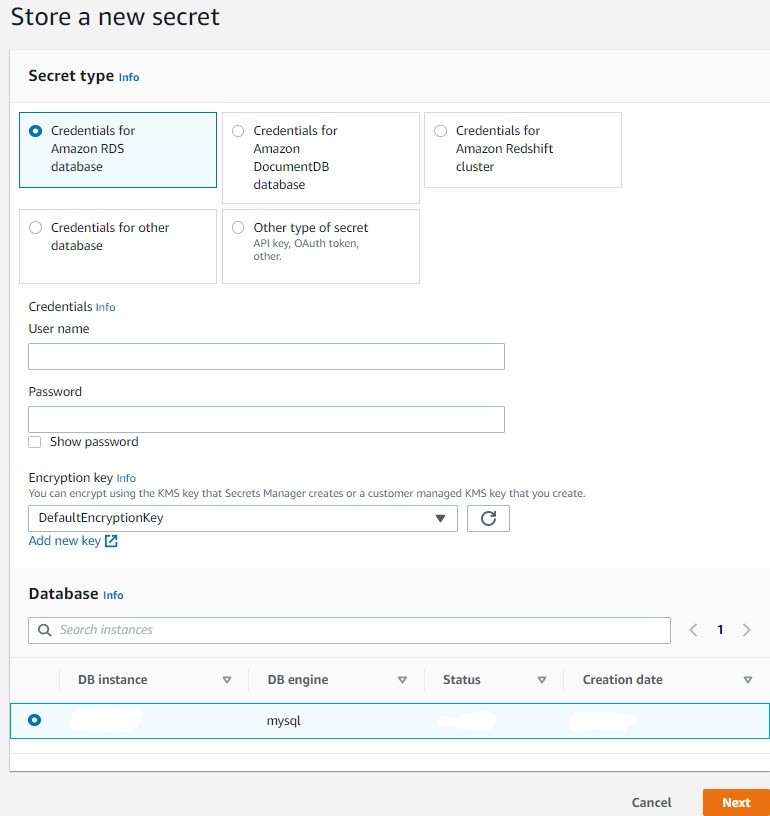
2. From Secret Type, select Credentials for Amazon RDS Database.
3. Type in credentials (Username and Password) which will grant access to Database.
4. Keep the Encryption Key as Default as Secrets Manager creates a default encryption key for the secret being created.
Note: It is also possible to create Customer Managed KMS Key and attach it to secret.
5. The Database section lists all the supported RDS Database which are there in AWS account. From the list select the RDS Database which was created initially and click Next.
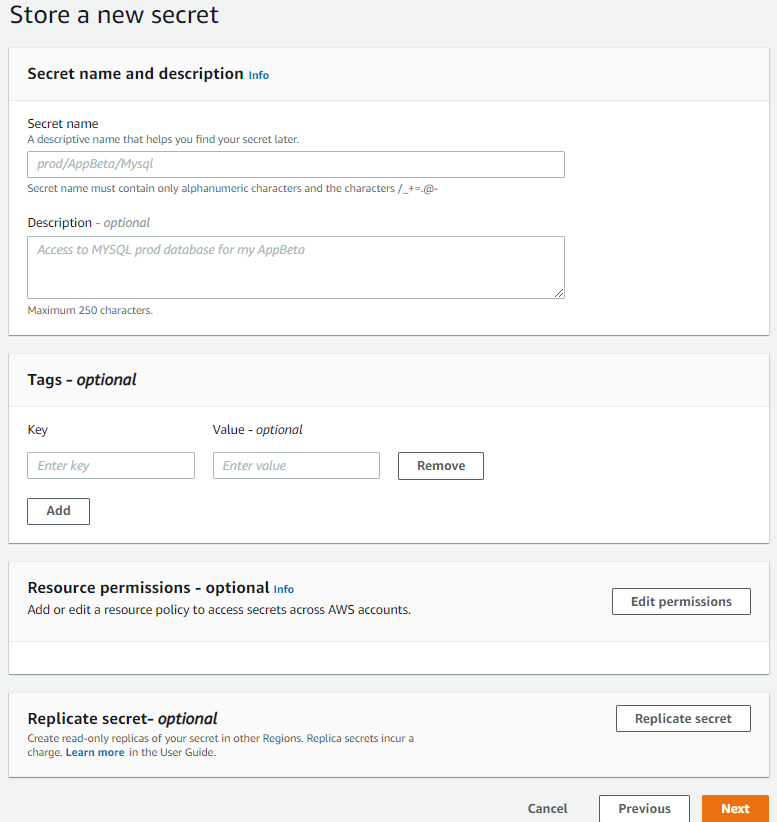
6. In this step, type in Secret Name and Description. The secret name can consist of path with “/” characters to enable the logical grouping of secrets. Eg:- “demo/demo1/*”.
Keep the rest of the settings as it is and click Next.
7. To enable rotation, select Automatic Rotation. Schedule a secret rotation by selecting Schedule expression builder and set Time unit from (Days/Weeks/Months). Under Window duration set the hour/s in which the rotation should take place. Below in the picture Time unit is 1 Days and Window duration is 1h which states that the secret will be rotated every day between 0:00 and 1:00 UTC+0.
Note: There are two strategies for secrets rotation, Single and Alternating user rotation. Here Single User Rotation Strategy is being used as this update’s credentials for one user in one secret.
8. From Rotation Function, select Create a rotation function and type in the Lambda function name in front of SecretsManager. Keep the secret credentials as No and click Next.
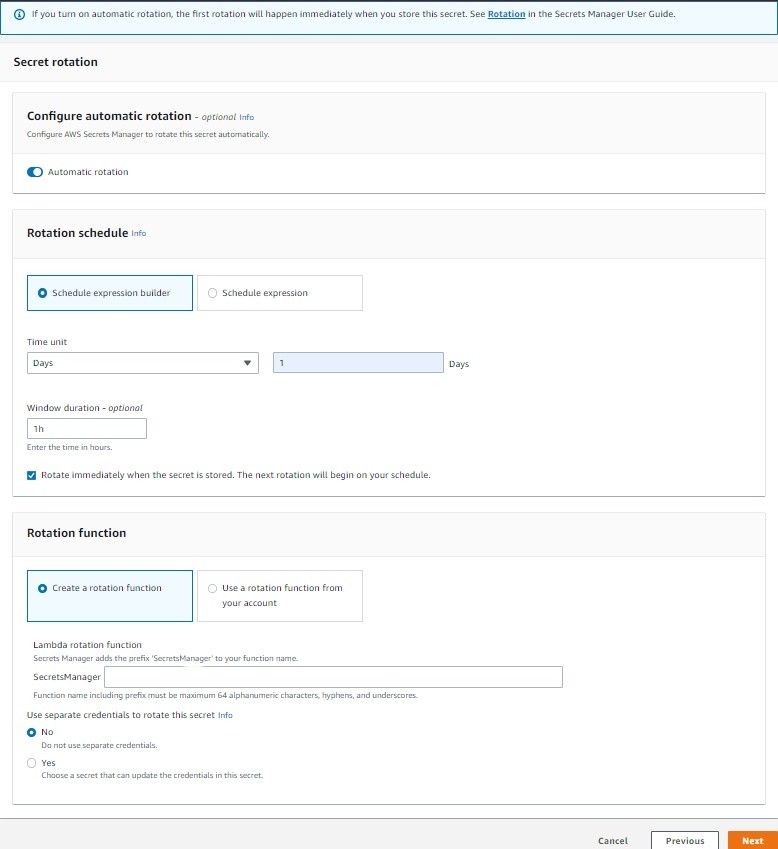
Note: It is necessary to create Lambda Function as this function will have right IAM policies and will add Secrets Manager under trusted entity which will invoke Secrets Manager based on the Schedule Expression builder.
Also, if you turn on automatic rotation, the first rotation will happen immediately when you store this secret.
9. Lastly, review the entire configuration and click Store.
10. While in the background, The Secrets Manager will launch CloudFormation stack consisting of Lambda Function which was created while Secret creation and will also create IAM role for invocation.
11. Once done, the Green banner on the next Secret Manager screen confirms that Rotation configuration is successful and the first rotation is in progress.

12. Following Secret has been created in Secrets Manager.
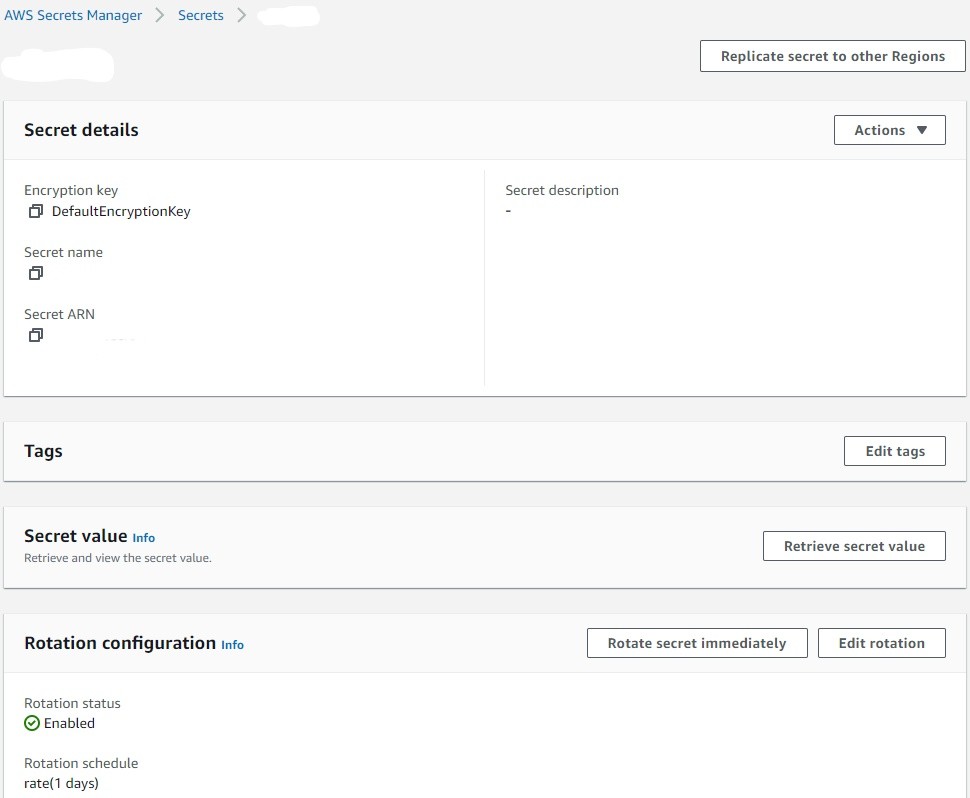
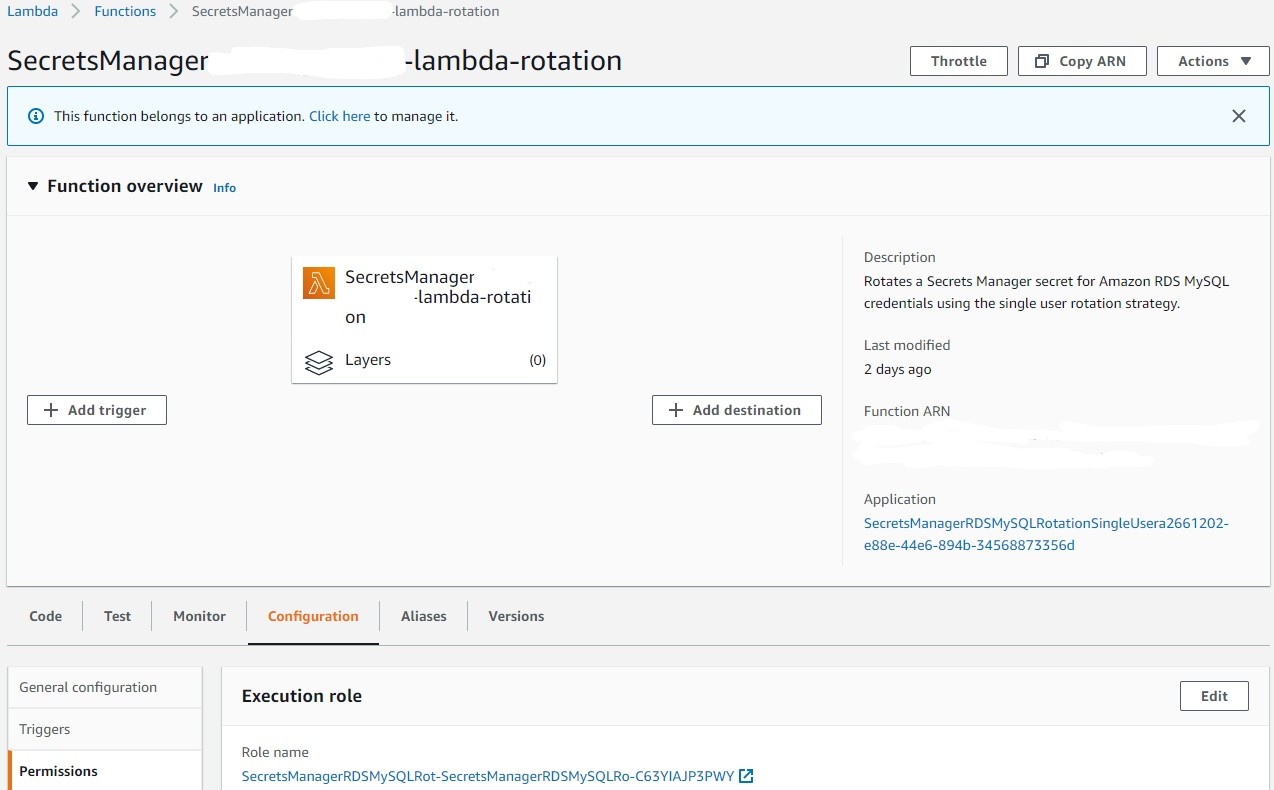
13. Below is the Lambda Function created by CloudFormation stack. This Lambda Function as mentioned above will follow the Single-user rotation scheme to rotate an RDS MySQL user credential. This rotation scheme logs into the database as the user and rotates the user’s own password, immediately invalidating the user’s previous password.

Leave a Reply